Being highly attentive to what is happening globally in cybersecurity is crucial. But, only if your company intends to surpass new susceptibilities and keep pace with the latest cybersecurity technologies and Cybersecurity Standards. According to Gartner’s survey, the core opinion leaders in cybersecurity anticipate the world to spend 11.3% more on risk & security management in 2024 than the previous year.
Companies nowadays have higher budgets for cybersecurity to tackle the hazards of branching out attack surfaces. It is significantly generated because of increasing teleworking, supply chain communications, cloud migration, and combining IT with IoT and OT.
With human flaws accounting for 95% of cybersecurity breaches, handling employee cyber risk is vital for your business to avoid user-based violations and show administrative adherence. Therefore, it is essential to prevent data breaches in 2024.
\Wondering how to do that? While protecting your business’s infrastructure, consider the following cybersecurity standards in 2024 to fight modern dangers.
What are Cybersecurity Standards?
Cybersecurity norms: Everything works differently in this highly dynamic and modernized era. If something works in one direction, other things might do the same by going in another direction. Therefore, the whole notion is the approach could be distinct; the work might still be accomplished.
Regarding cybersecurity, everyone trusts in implementing their own set of regulations. Still, as everyone uses the internet globally, countless norms must be unaltered, irrespective of where the World Wide Web is employed.
Read also: GridinSoft Anti-malware Review: The Final Layer of Security for Windows
Top 10 Cybersecurity Standards to Thwart Cyber Attacks in 2024
As cybersecurity is one of the most crucial factors in protecting organizational data, whether a small or big enterprise. Everyone desires to secure administrative data. Regarding the type of data that needs protection, there are several Cybersecurity standards. Below are the top 10 cybersecurity standards to thwart cyber-attacks in 2024.
HIPAA
The complete form of HIPAA is Health Insurance Portability and Accountability Act, which is the norm that healthcare sectors follow to ensure that their patient’s data are safeguarded and one cannot breach it. The medical facilities must build a powerful network safety team to adhere to this standard and handle every security incident.

Their quarterly safety reports must be updated and top-notch, and every transaction should be encoded. This HIPAA guideline ensures that the vital health-based details of the patient will be kept protected so that the patient can feel protected about their health.
FISMA
FISMA is the shortened form of the Federal Information Security Management Act, a US federal regulation authorized as Title III of 2002’s Government Act. This legislation sets up a more comprehensive framework for ensuring the safety details for every executive branch bureau. This FISMA reinforced information security within federal companies, OMB, and NIST.

To safeguard the safety, reliability, and accessibility of their data and computer networks, regardless of whether they are supplied or controlled by other government departments or independent contractors, it mandates that federal organizations put data protection programs into place.
GDPR
GDPR, aka The General Data Protection Regulation, was enacted in 2016 to bolster data protection processes for EU residents. This cybersecurity standard influences every organization put in place in the EU or any agency that gathers and preserves the confidential data of EU dwellers, including US companies.

Moreover, this well-known cybersecurity standard consists of 99 articles referring to a business’s adherence liabilities, including a customer’s data access rights, procedures, protection norms, data breach notification needs, etc. Up to €20,000,000 or 4% of the worldwide revenue can be fined for disregarding them, and the EU is not afraid to enforce these penalties.
ISO/IEC 27032
ISO 27032 is a widely known guideline offering assistance on cybersecurity for companies. The norm is created to aid companies in safeguarding themselves against cyber-attacks and regulating the dangers linked with technology employment.

You must thwart a cyber-attack by installing an SSL certificate for data safety. It can be a budget-priced single-domain SSL, multi-domain SSL, or a cheap wildcard SSL. However, this guideline is based on a risk management strategy that offers assistance to identify, evaluate, and regulate cyber risks. Finally, yet importantly, this prestigious cybersecurity benchmark additionally comprises help with disaster response and restoration.
PCI DSS
The complete form of PCI DSS is the Payment Card Industry Data Security Standard, which needs to be chosen by the company that embraces payment through its portal. Those enterprises keep user data, for example, their name and card details, based on information needed to adopt this guideline.

Regarding compliance, the cutting-edge technologies employed by the enterprises must be updated, and their system must be prepared to perform safety evaluations to ensure that it does not have any significant vulnerabilities. American Express, JCB, Visa, Discover, and MasterCard are renowned card brands that have developed this cybersecurity standard.
NERC-CIP
This cybersecurity standard has been established to decrease the surge in cyber-attacks on the vital infrastructure of US companies and ongoing third-party attacks. Moreover, it’s a revamped set of cybersecurity guidelines crafted to help people in the power & utility sector mitigate cyber threats and ensure the credibility of massive electric systems.

This policy mandates a wide range of laws and regulations, including essential resources and classifying infrastructure, incident management, training personnel, organizing and recollection plans for necessary cyber resources, susceptibility evaluations, and more. It also requires influential companies to identify and reduce nefarious third-party cyber hazards in their supply chain.
NIST CSF
NIST CSF, aka National Institute of Standards and Technology Cybersecurity Framework, is a voluntary standard offering a broad spectrum of guidelines and practices for regulating cybersecurity risks.
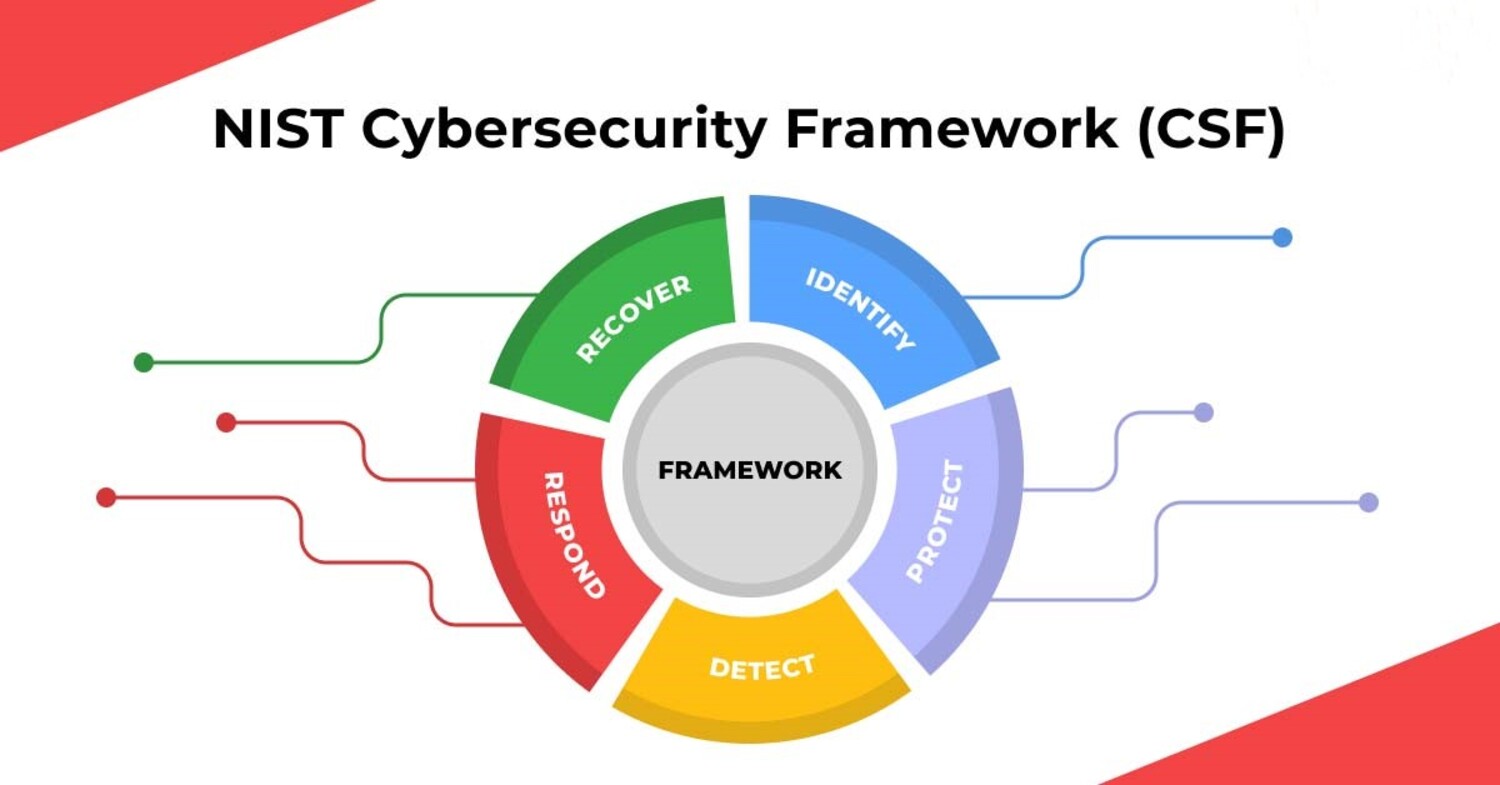
These guidelines aid companies in discovering, evaluating, and controlling their cybersecurity hazards in an iterating and structured way. Although following the NIST CSF guidelines is not required, businesses increasingly embrace them as an optional strategy to strengthen their safety measures.
ISO 27001
It is a general cybersecurity standards complying with the company to implement a data safety regulation system. Moreover, it includes many processes defining the guidelines and needs that must be met to get the company certification.

According to this cybersecurity standards, the company must preserve every updated technology, the servers must exist without susceptibilities, and the company needs to be audited after the particular intermission to adhere to this standard. Moreover, every business that supplies other companies that abide by the widely recognized worldwide standard ISO 27001 must comply with the ISMS principles safeguarded by this standard.
Check this out: Increase Your Home’s Security With Modern Technology: SpotCam HD Eva
SOC2
SOC Type 2 refers to Service Organization Control, a trust-oriented cybersecurity guideline and auditing norm created by the American Institute of Certified Public Accounts (AICPA to help assess if the partners and vendors are safely controlling customer data. SOC2 indicates over 60 adherence needs and a broad array of auditing stages for third-party controls and systems. One may require a year to finish an audit.
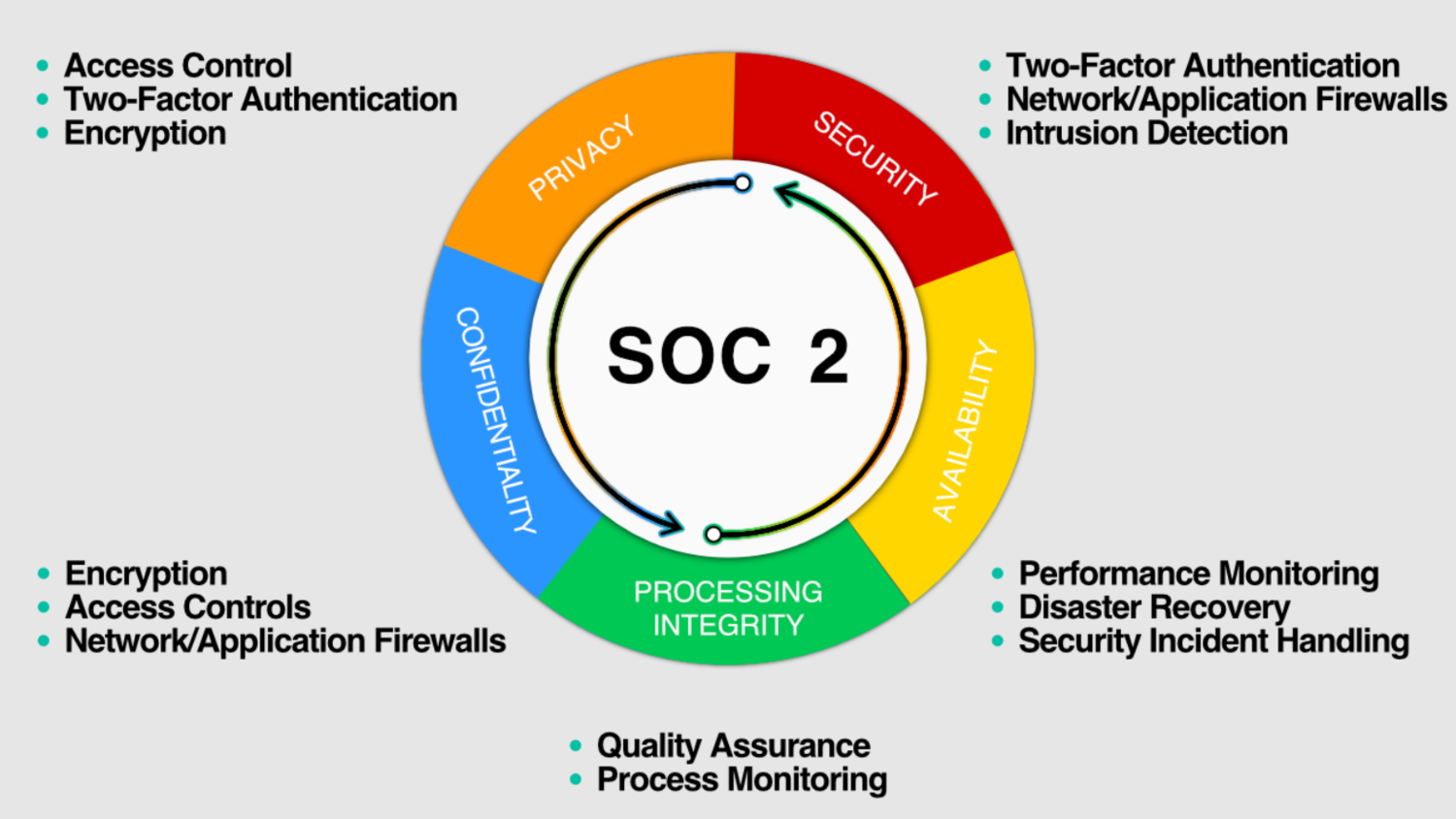
A document is then published attesting to a vendor’s cybersecurity status. SOC2 is the most challenging standard to implement due to its magnitude – mainly for companies in the banking or finance sector who encounter a higher norm for adherence than other sectors. However, SOC2 is a critical structure that needs to be at the heart of risk mitigation plans.
DFARS
DFARS, aka Defense Federal Acquisition Regulation Supplement. It is a set of detailed norms applying to every US Department of Defense or DOD subcontract and contract. DFARS is carefully created to ensure this department gets top-notch merchandise and services at nominal rates.

It consists of a wide array of cybersecurity needs that contractors must fulfill, which includes the following:
- Setting up a cybersecurity program consists of stipulated safety controls and procedures to safeguard data from third-party access, disruption, and misuse.
- Guarantee that every employee and vendor connected with DOD information or systems has the appropriate training and security authorization.
- Putting in place a framework for identifying, evaluating, and mitigating risks related to DOD systems and information.
- Verifying that every DOD system and detail is adequately safeguarded from malicious third-party access and disclosure.
- Creating and implementing the right strategy to respond to incidents and cyber-attacks could endanger DOD systems or data.
- Implementing transparency and auditing procedures to maintain the safety of DOD technology and information.
Conducting business with the DOD requires contractors, subcontractors, and government purchasing authorities to abide by the DFARS.
Conclusion
In 2024, it is expected that the growth of cloud security, the increasing utilization of the zero trust model, a surge in cybersecurity compliance needs, threat identification, and response techniques.
To regulate new looming threats of OT, supply chains, remote work, IoT, and the cloud, you must adhere to these top 10 cybersecurity standards described here. Moreover, nearly every company that performs at an elevated level must adhere to the guidelines as the elements guarantee the organization’s privacy.
See also: How to Become a Physical Security Consultant in 6 Steps
He is a Tech Geek, Gadget Expert, SEO Expert, Web Designer, and a Blogger. Having a technology background gives him a unique perspective!